Password databases: Installing password-store on Android
The final part of the password puzzle is getting my passwords into my pocket. There are quite a few images in this post (about 2MB) as I describe setting up the system on Android, which involves a lot of steps, with screen-shots.
Hold onto your hat, it's a bit of a fiddle.
The Password Store system for Android
Here are all the parts of the Password Store system, as installed on Android. It's similar to the Unix Password Store system but differs in how SSH and PGP have been packaged into utilities.
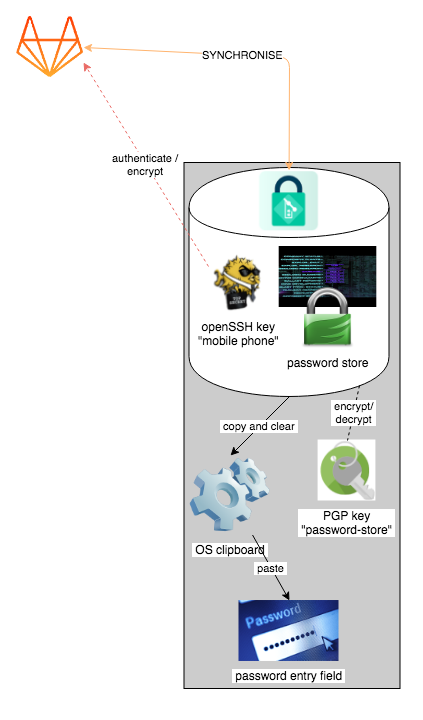
Password-Store Android tool chain — see a vector rendition
There are two apps involved in the system, both are fairly small and don't need many computrons, so they are no trouble to have even on a smallish droid phone (my cheap drop-and-don't-cry Alcatel Pop4 manages these fine):
- Password Store — manages your password store in your phone, with sync to remote git repository via SSH authentication
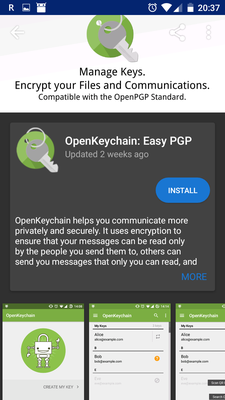
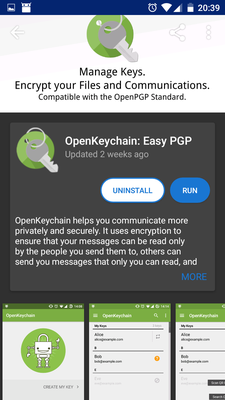
- OpenKeychain — does the actual cipher work and manages PGP keys on your phone. Can encrypt/decrypt files or be called from other apps like Password Store.
Setting up Password Store on an Android
There are a lot of steps here. I do this is four stages
- Install the software
- Transfer the PGP keys for the password store into the phone
- Set up the software and perform first clone
- Test creating a password on the phone and synchronise to a PC
Fortunately you only need to do this once per phone system, and once installed the actual operation is much simpler. Remember why I'm using Password Store:
- Smarter merges for individual password changes, rather than sync the whole database
- Better control over where my passwords are stored on the Net and how they are accessed
- Potential for fine-grained access control in the future
And some bonus features:
- Can track individual password changes
- OpenKeychain provides PGP encryption for other purposes
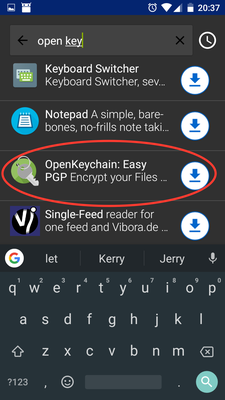
1. Install the software
On the Android, follow these steps:
-
(optional) Install F-droid since the Google Play Store version of Password Store has been crippled upon Google's request (auto-fill disabled)
-
Install Password Store from Google Play or F-droid:
-
Install OpenKeychain from Google Play or F-droid:
2. Transfer the PGP keys to the phone
There are some different ways to do this. I use email and send them to myself as an attachment, PGP encrypted for the phone. So if my email is intercepted, or read by Google, the password store keys can't be stolen.
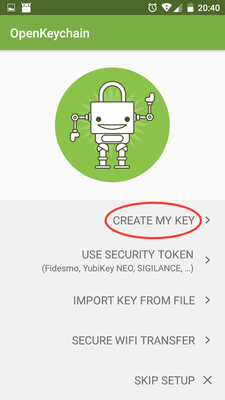
- First set up a new PGP key on my phone, and send the public key to myself.
- Then I can encrypt the password store's keys with my phone as Recipient and email those back.
Here are the steps:
-
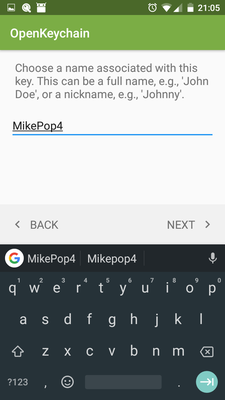
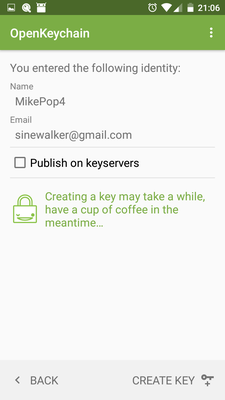
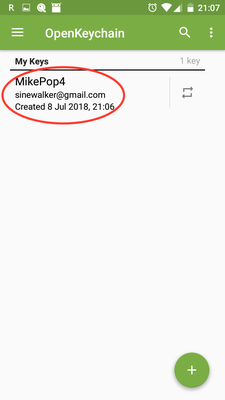
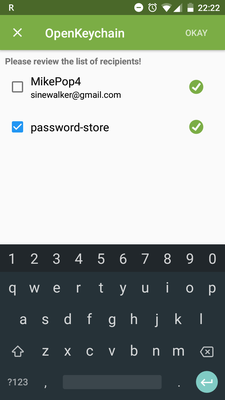
In OpenKeychain, generate a new key, e.g.
MikePop4 -
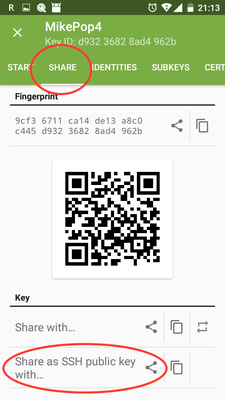
Send the key to yourself by email (it sends the public key only)
The next four steps occur on your PC / Mac. Open your email on the PC/Mac, and save the email attachment.
- Import the key to the PC/Mac keychain and Trust it's Ownership
[mjl@milo:~/Downloads] [21:26]β gpg --import MikePop4.asc gpg: key D93236828AD4962B: public key "MikePop4 <sinewalker@gmail.com>" imported gpg: Total number processed: 1 gpg: imported: 1 [mjl@milo:~/Downloads] [21:26]β
- Export your
password-storepublic and secret key pair to some place secure (e.g. the Keybase KBFS, then you won't have to re-export from another PC in future):
[mjl@milo:/keybase/private/sinewalker/key/gpg] [21:28]β gpg --export --armour password-store > password-store.sec.asc [mjl@milo:/keybase/private/sinewalker/key/gpg] [21:28]β gpg --export-secret-keys --armour password-store >> password-store.sec.asc
- Encrypt the exported Password Store key pair for `MikePop4``
[mjl@milo:/keybase/private/sinewalker/key/gpg] [21:29]β gpg --trust-model always -e -r MikePop4 password-store.sec.asc [mjl@milo:/keybase/private/sinewalker/key/gpg] [21:29]β
- Email
password-store.sec.asc.gpg(encrypted for your phone) to yourself
Switch back to the phone, open the mail and save the email attachment
3. Set up Password Store
Phew! At this point, we have the software and the PGP key pair on the phone. Now to get the actual password store.
- Make sure you have run
pass git push allat least once on the PC, to push your encrypted Password Store to your online remote
On the phone, open Password Store and:
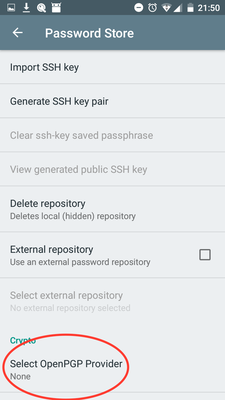
-
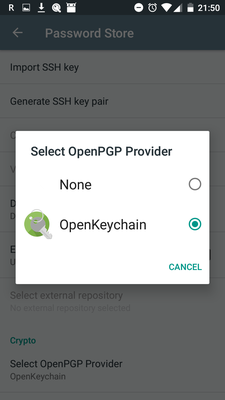
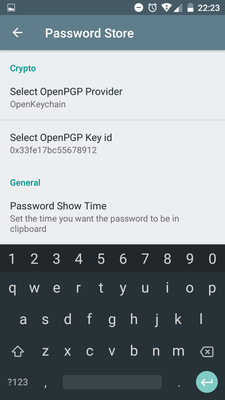
Go to Settings, Select OpenPGP Provider and choose OpenKeychain
-
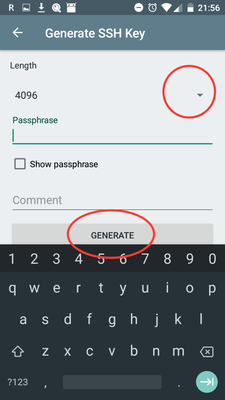
Generate SSH Key (this is to authenticate to the git remote)
-
When the Public SSH key is displayed, touch COPY to put it on your phone's clipboard
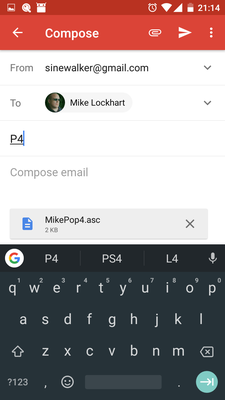
-
Email your phone's public SSH key to yourself (Paste into the email)
-
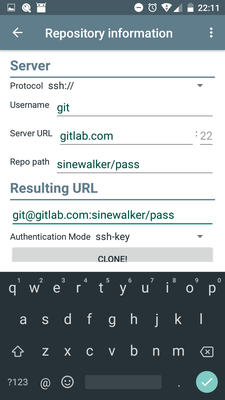
In Gitlab (or which ever Remote you use), register the public key with your private repo
-
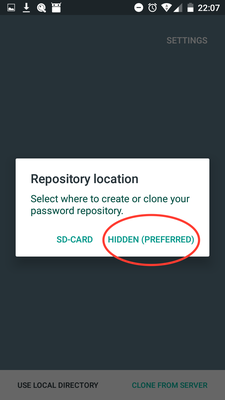
In Password Store on the phone, CLONE FROM SERVER, choose HIDDEN(PREFERRED) (stores internal to the app)
-
Test viewing a password
- Password Store will request to use OpenKeychain as a crypto provider. This is what you asked for, so ALLOW
- Password Store* will next request access to your
password-storekey. This is expected, ALLOW
- Enter the passphrase for your
password-storekey (you do this each time you view a password, so if your phone is stolen your passwords are still safe, protected by this passphrase)
If your password displays, congratulations! Now you have access to your passwords in your pocket.
4. Test password creation and syncing
You should probably test syncing back to base
-
Create a password. Password Safe will redirect you to chose a key to encrypt with. Use
password-store -
Push to your git remote
On your PC, pull and test decrypt. Then you can remove the test password and push back:
[mjl@milo:~] [22:09]β pass git pull remote: Counting objects: 5, done. remote: Compressing objects: 100% (5/5), done. remote: Total 5 (delta 3), reused 0 (delta 0) Unpacking objects: 100% (5/5), done. From gitlab.com:sinewalker/pass 0baca19..6e7b75b master -> origin/master Updating 0baca19..6e7b75b Fast-forward home/tesla/test.gpg | Bin 0 -> 878 bytes 1 file changed, 0 insertions(+), 0 deletions(-) create mode 100644 home/tesla/test.gpg [mjl@milo:~] [22:25]β pass home/tesla/test Xoowaerahd1Oi7ohKeil [mjl@milo:~] [22:25]β pass rm home/tesla/test Are you sure you would like to delete home/tesla/test? [y/N] y /Users/mjl/.password-store/home/tesla/test.gpg [master 3cb98d6] Remove home/tesla/test from store. 1 file changed, 0 insertions(+), 0 deletions(-) delete mode 100644 home/tesla/test.gpg [mjl@milo:~] [22:25]β pass git push Counting objects: 4, done. Delta compression using up to 4 threads. Compressing objects: 100% (4/4), done. Writing objects: 100% (4/4), 374 bytes | 374.00 KiB/s, done. Total 4 (delta 3), reused 0 (delta 0) To gitlab.com:sinewalker/pass 6e7b75b..3cb98d6 master -> master [mjl@milo:~] [22:25]β
You now have secure, two-way syncing between your phone and your other computers, with the shared encryption keys, using Git+SSH on an online private Remote.
Happy Hacking.